Join a meeting without an account in Microsoft Teams
You can join a Teams meeting anytime, from any device, without signing into a Teams account.
If you’re having trouble joining a Teams meeting, try I can’t join a Teams meeting.
Important: For some meetings, admin settings prevent unverified people from joining the meeting. Depending on the meeting, you may have to enter a one-time passcode sent to your email or create a Teams account.DesktopMobile
Join the meeting before it starts to test your setup from the pre-join screen. From there, you can enter the meeting up to 15 minutes before its start time to troubleshoot or see how Teams works. Meeting participants and organizers will be notified when you enter the meeting.
To join a Teams meeting without signing into an account:
- Open the meeting invite and select the link next to Join or Click here to join the meeting.
- When prompted, select Continue on this browser or Join on the Teams app. You don’t need to install the Teams app to join the meeting.
- You can join Teams for web on Microsoft Edge or Google Chrome. You may be prompted to give Teams access to your mic and camera. When you select Allow, you can always turn off your mic and camera once you join the meeting.
- Select Join now.
- In meetings where admin settings prevent unverified people from joining, you’ll be prompted to enter your email address. Enter your email address and select Next. Enter your password if you already have a Microsoft account or select Send code and enter the one-time passcode sent to your email if you don’t have an account. Once verified, select Join now.
Note: People who are signed in will have access to more meeting features than those who aren’t signed in.
If you enter the meeting lobby, wait for someone in the meeting to admit you. If no one admits you within 30 minutes, you’ll be removed from the lobby. If that happens, you can try rejoining.
Depending on how you joined the meeting, other participants will see a label next to your name. If you joined:
- without entering your email address, everyone will see Unverified next to your name.
- using a one-time code sent to your email, everyone will see Email verified next to your name.
- with your Microsoft account, everyone will see External next to your name.
Organizer’s view
If you’re the meeting organizer, we’ll alert you when someone is waiting in the lobby.
Select Admit to let them right into the meeting, or View lobby to see a list of everyone in the lobby and admit or deny them.
Note: Anyone who doesn’t have a Teams account and joins the meeting without entering a one-time passcode sent to their email will be labeled Unverified. Anyone who doesn’t have a Teams account and joins the meeting after entering a one-time passcode sent to their email will be labeled Email verified. To learn more about people with guest access, see Work with external guests.
I can’t join a meeting in Microsoft Teams
If you can’t immediately join a Teams meeting, there are several possible reasons:
- You’re waiting in the lobby: Some organizers might place attendees in a lobby before admitting them into the meeting. Wait for someone to admit you, or reach out to the organizer directly to be let in.
- Your internet browser isn’t supported: Teams doesn’t currently support Safari for Mac. If you’re joining a Teams meeting from the web, try joining from Microsoft Edge, Google Chrome, or other supported browsers.
- Your internet connectivity is low: If your internet connection is low, you may not be able to join a Teams meeting right away. Try waiting for your connection to improve, joining from your supported mobile device, or reaching out to your internet provider.
- Security policies for the meeting are preventing you from joining: If a meeting organizer enables end-to-end encryption for a meeting, you might have limited access to join. Try reaching out to the organizer to be let in.
In Teams, you might receive a message about why you’re unable to enter a meeting. Here are the different messages you might encounter and how to resolve them.
“Sign in to join this meeting”
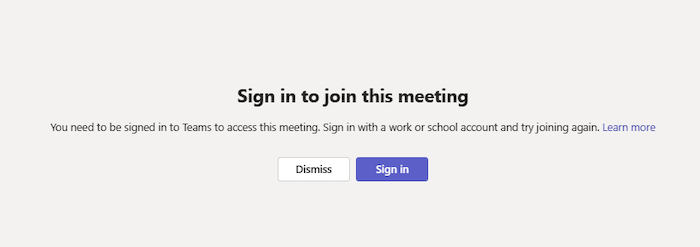
If you see this message, the meeting doesn’t allow people to join unless they’re signed in with a Teams work or school account. You might need to take extra steps to join:
- If you’re joining from a meeting link or as an anonymous user, make sure you’re signed into your Teams work or school account.
- If you’re the meeting organizer and want people to be able to join your meeting without signing in, contact your IT admin (learn more here). Changes from your IT admin may take up to 24 hours to take effect.
“Sign in with a different account to join this meeting”

If you see this message, the policies set by your or the meeting organizer’s org prevent you from accessing the meeting. You might need to take extra steps to join:
- Make sure you’re signed into the account the invite was originally sent to.
- If you’re the meeting organizer and you want to allow people from other orgs to join your meeting, contact your IT admin (learn more here). Changes from your IT admin may take up to 24 hours to take effect.
“This meeting is locked.”
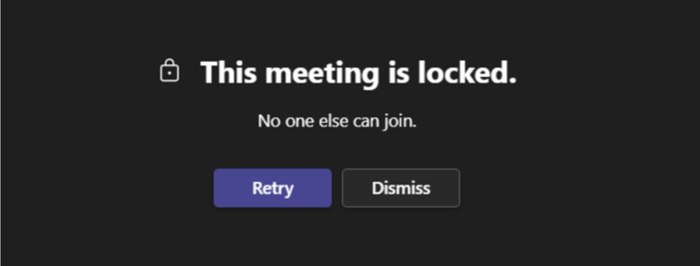
After a meeting starts, organizers can lock the meeting to prevent new participants from entering.
Reach out to the meeting organizer to let them know you’re having trouble joining. If they unlock it, you can try joining again.
“Your organizational policy does not allow you to join this meeting”
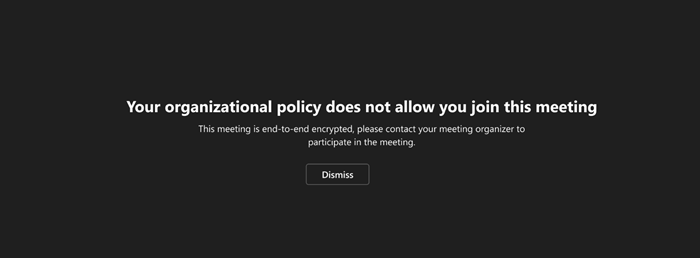
You can’t join because the organizer has enabled end-to-end encryption for their meeting. Contact the organizer to let them know you’re having trouble joining.
“The meeting lobby is full right now.”
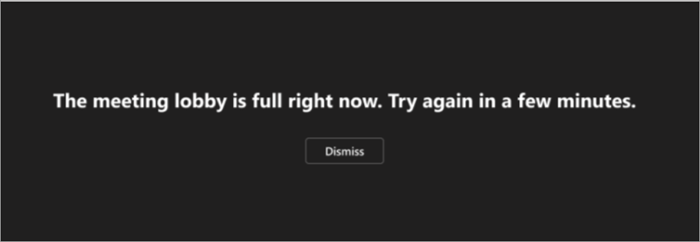
If the lobby is full, wait a few minutes before trying to join again. You may be able to enter if other attendees join the meeting or leave the lobby. For more on lobby settings, see Using the lobby in Teams meetings.
“Sorry, no one has responded to your request to join.”

If you get this message after 30 minutes of waiting, your request has timed out.
- Check to make sure you’re joining from the correct meeting link and try again.
- Reach out to the meeting organizer to make sure your request is seen.
Using the lobby in Microsoft Teams meetings
Use the meeting lobby in Teams meetings to keep people from directly entering a meeting when they join. Organizers, co-organizers, and presenters will be notified when people enter the lobby and can let them into the meeting.
In this Section
- Lobby settings
- Lobby notifications
- Change lobby settings
- Turn off the lobby
- Manage lobby
Lobby settings
Each meeting defaults to the lobby settings set by your IT admin but you can change them before or during the meeting. You might not be able to change some settings if your meeting uses a template or sensitivity label.
Choose who can bypass the lobby
As the meeting organizer, you get to decide who gets into your meetings directly, and who should wait for someone to let them in.
If you choose to have people wait, you (and anyone else allowed to admit people) will see a list of people in the lobby. From there you can choose whether to admit or deny them.
| Who can bypass the lobby? | What happens | Recommended when… |
|---|---|---|
| Only organizers and co-organizers | As the meeting organizer, you and any co-organizers can get into the meeting directly. Everyone else will wait in the lobby. | You want everyone else to wait in the lobby until you’re ready to admit them. |
| People who were invited* | Anyone who receives the invitation, including those to whom it is forwarded, will join the meeting directly.People without a Teams account won’t bypass the lobby. Additionally, distribution lists up to 10,000 users are supported. If you don’t want people to forward the invite to others, turn off Allow Forwarding in the invitation. | You want a specific, limited group of people who were invited via their Teams accounts to join the meeting directly, and everyone else to wait in the lobby. |
| People in my org | Only people within your org can get into your meeting directly. Everyone else will wait in the lobby. | You want all guests and external people to wait in the lobby so you can approve them one by one. |
| People in my org and guests | People in your org and people with guest access can get into your meeting directly. | You want all external people (anyone outside your org, except guests) to wait in the lobby so you can approve them one by one. |
| People in my org, trusted orgs, and guests | Anyone from your organization and organizations with which your IT admin has set up a connection, or anyone joining as a guest, will be able to bypass the lobby. | You want some external people (e.g., people joining without a Teams account and people from organizations with which your IT admin did not set up a connection) to wait in the lobby so you can approve them one by one. |
| Everyone | Anyone who has access to the meeting link gets into the meeting directly, including people who call in.Depending on the meeting policy set up by your IT admin, people joining without a Teams account,people from untrusted organizations, and people dialing in may be placed in the lobby until someone from your organization or a trusted organization joins the meeting, even if the Everyone option is selected. | You don’t want anyone to wait in the lobby. You want everyone to be able to join your meetings without specific approval. |
* For channel meetings, only those channel members who are directly invited can bypass the lobby.
Change lobby settings
You can change lobby settings before, during, or after a meeting (in the case of a meeting series). The changes will only apply to the meeting you change them in unless the meeting is part of a series. Then, changes will be applied to all future meetings in that series. To change default lobby settings, contact your IT admin.
Before a meeting
Before a meeting
New calendar
To change lobby settings before a meeting:
- Select Calendar
in Teams.
- Double-click an event.
- Select Edit
.
- If you double-clicked an instance of a meeting series, select whether you want to edit This event, This and all following events, or All events in the series.
- Select Meeting options
.
- In Meeting access
:
- Choose an option from the Who can bypass the lobby? dropdown menu.
- Turn the People dialing in can bypass the lobby toggle on or off.
- Choose who can let people into the meeting from the Who can admit from the lobby dropdown menu.
- Select Save.
To learn more about the new Teams calendar, see Get started with the new calendar in Microsoft Teams.
During a Meeting
During a meeting
If you change lobby settings during a meeting, people waiting in the lobby will still be there.
Select Save.
Select More actions > Settings > Meeting options
in your meeting controls.
In Security:
Choose an option from the Who can bypass the lobby? dropdown menu.
Turn the People dialing in can bypass the lobby toggle on or off, if available.
Choose who can let people into the meeting from the Who can admit from the lobby dropdown menu.
Manage the lobby
During a meeting, people you designated to manage the lobby can admit or deny entrance to the meeting.
Who can manage the lobby
The meeting organizer, co-organizer(s), and presenter(s) can manage the lobby. If you’re the organizer, choose which of those roles can manage the lobby during that specific meeting. You can also make someone a co-organizer or presenter by changing their meeting role.
To change who can manage the lobby:
- Select Calendar
in Teams.
- Double-click an event.
- Select Edit
.
- If you double-clicked an instance of a meeting series, select whether you want to edit This event, This and all following events, or All events in the series.
- Select Meeting options
.
- In Meeting access
, choose who can let people into the meeting from the Who can admit from the lobby dropdown menu.
- Select Save.
To learn more about the new Teams calendar, see Get started with the new calendar in Microsoft Teams.
Admit or deny participants
During the meeting, people managing the lobby can see a list of participants waiting to get into the meeting and choose whether to admit or deny them.
To admit or deny participants:
- Select People
in your meeting window.
- Under Waiting in the lobby:
- Select the check mark next to someone’s name to admit them.
- Select the X next to someone’s name to deny them.
- Select Admit all to let everyone in from the lobby.
Lobby notifications
People managing the lobby will receive notifications that people are waiting in the lobby. In the notifications, select View lobby to go right to the lobby or Mute these notifications to turn the notifications off.
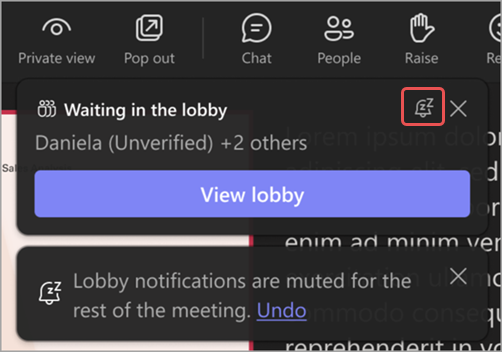
Select Undo to turn the notifications back on.
Turn off the lobby for a meeting
If you want everyone to join your meeting directly, set Who can bypass the lobby? to Everyone. This change will apply to that meeting and future meetings if it’s part of a meeting series. Contact your IT admin if you want to change this setting for all the future meetings you organize.
Note: If anonymous participants join first, they’ll wait in the lobby. They’ll be let into the meeting automatically after someone from your org, a trusted org, or a guest user joins. Contact your IT admin to allow anonymous participants to start meetings.
You can also remove people or lock your meeting.
To remove people from the meeting:
- Select People
in your meeting window.
- Hover over the name of the person you want to remove.
- Select More options > Remove from meeting.
Applies To
Try it!
Guests have similar capabilities to team members and can participate in meetings, chats, and work on documents.
- In a team, select More options>Add member.
- Enter the guest’s email. You can add as many guests as you need.
- If needed, it’s best to change their display name now.
- When ready, select Add and guests will be sent an email invitation they need to accept to begin.
A guest will have the label “Guest” attached to their name in Microsoft Teams. You can also check the top of any channel to see how many guests are in it.
To share files, use the Files tab and folders since document links may not work with guests.
Note: Before guests can join a team, an admin must enable guest access in Teams. If you can’t add a guest, check with your admin.