Get the most out of OneNote with these little-known features
Hi, Microsoft 365 Insiders! I’m Gokul Subramaniam, and I’m a Product Manager on the OneNote team. If you’re a OneNote fan, you’re aware of the many ways it can streamline and boost note-taking and content generation. But even the most experienced OneNote users among us might not be benefitting from all it has to offer, which is why we’ve singled out some of our favorite features that you may not be aware of – or wish existed but didn’t know they already did. Check them out, supercharge your productivity, and let us know what you think!
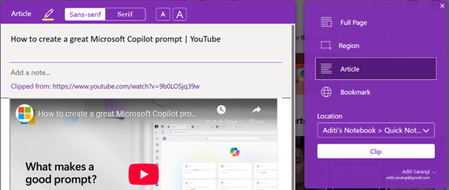
With OneNote Web Clipper, you can easily capture and save online materials directly into your OneNote notebooks, saving you time manually copying information and allowing you to preserve the content in its original form. By simply adding the OneNote Web Clipper extension to your preferred browser, you can instantly begin clipping articles, recipes, YouTube videos, or other types of web pages, and neatly organize them into your notes for reference later.
The print to OneNote feature enables you to send any type of file, including documents, spreadsheets, emails, drawings or diagrams, web pages, and PDFs, directly to a OneNote notebook as a printout. This can be particularly useful for students saving lecture notes, professionals archiving important reports or correspondences, and anyone else wanting to keep a digital copy of physical documents for easy access and annotation. Simply select Print on the file, and then choose OneNote (Desktop) or OneNote (Desktop) – Protected in the Printer list to add it as an image in your chosen notebook or page.
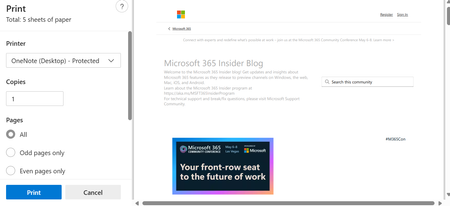
Availability: This feature is only available to OneNote on Windows users.
Made a mistake or written over crucial content in OneNote? You can restore previous versions of your notes, ensuring that all important information is not lost for good. Perhaps most crucially, this feature gives you peace of mind that should someone else have access to your notebook and make edits, you can still go back to earlier versions if you don’t like what they’ve added. Try it out the next time you want to track progress on a school essay, or revisit old versions of a work project, or revert back to an earlier draft. Under History, you can locate a version of your notebook based on timeframe or author, view all previous page versions, and delete certain versions you no longer need.
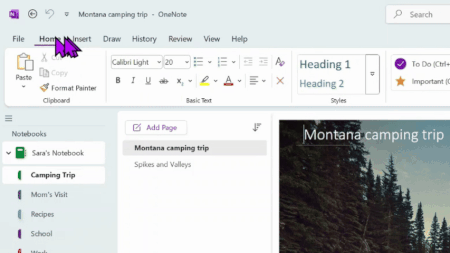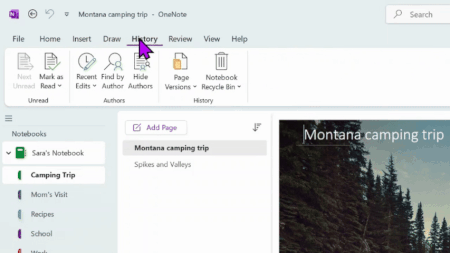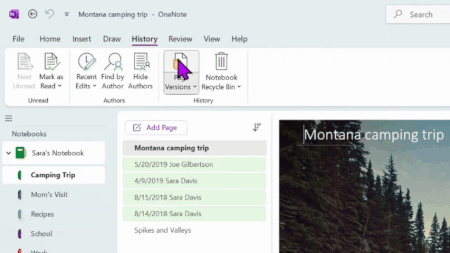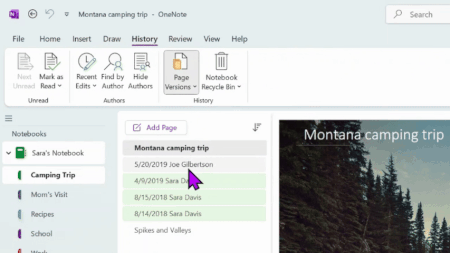
Availability: This feature is only available to OneNote on Windows, OneNote for Mac, and OneNote for the web users.
The Recycle Bin in OneNote is a feature that temporarily stores deleted notes and sections, allowing users to recover content that’s valuable or has been accidentally removed. Items in the Recycle Bin can be restored to a specific location in your notebook or permanently deleted, providing an additional layer of security against unintentional data loss. For instance, you can bring back mistakenly deleted project plans, or pull out discarded meeting notes, from the last 60 days.
Availability: This feature is only available to OneNote on Windows, OneNote for Mac, and OneNote for the web users.











